Which of the following should an administrator implement to research current attack methodologies?
A. Design reviews
B. Honeypot
C. Vulnerability scanner
D. Code reviews
Answer: B. Honeypot
Computer Science & Information Technology
You might also like to view...
A pointer variable is designed to store
A) any legal C++ value. B) only floating-point values. C) a memory address. D) an integer. E) None of the above
Computer Science & Information Technology
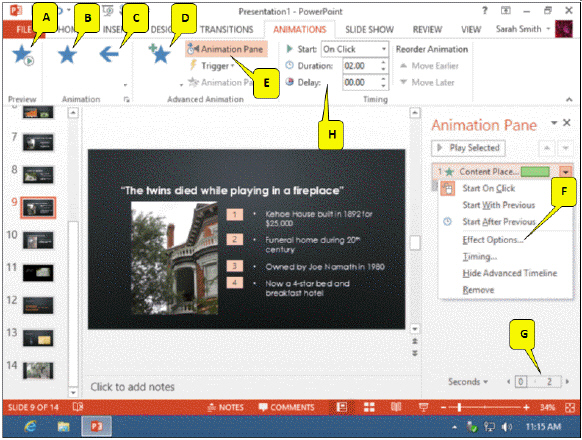 Referring to the figure above, which callout points to the option used to customize the animation?
Referring to the figure above, which callout points to the option used to customize the animation?
A. D B. E C. F D. G
Computer Science & Information Technology
What are some of the typical server attacks used by attackers?
What will be an ideal response?
Computer Science & Information Technology
All Microsoft Office programs have a share button except PowerPoint.
A. Yes B. No
Computer Science & Information Technology