Let the function 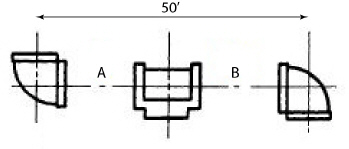 . Find
. Find 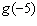 .
.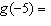 __________
__________
Fill in the blank(s) with the appropriate word(s).
-20
Computer Science & Information Technology
You might also like to view...
When an arithmetic operation yields a result too large to be represented by the expression's data type, _____ occurs.
a. arithmetic underflow b. arithmetic overflow c. cancellation error d. mantissa expiration
Computer Science & Information Technology
The first elements you add are ______ elements, which are elements that contain content that is viewed as a distinct block within the Web page.
A. grouping B. structural C. heading D. paragraph
Computer Science & Information Technology
A ________ is a group of applications bundled together by software companies to allow for special pricing
Fill in the blank(s) with correct word
Computer Science & Information Technology
List at least four things that a vulnerability scanner can do.
What will be an ideal response?
Computer Science & Information Technology