Browse the Internet and perform a search on “prevent SQL injection attacks”. What are 2 methods or steps that can be taken to prevent SQL injection attacks?
What will be an ideal response?
Filter user input
Deploy a web application firewall
Disable unnecessary database features/capabilities
Monitor SQL statements
Use parameters with stored procedures
Use parameters with dynamic SQL
You might also like to view...
Characteristics of a field that control how the field displays and how data is entered are:
a. data sources b. data forms c. field properties
A ____ variable can hold only "true" or "false" values.
A. static B. Boolean C. numeric D. String
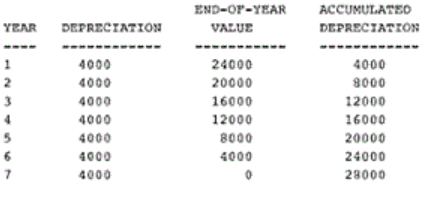
A machine purchased for $28,000 is depreciated at a rate of $4000 a year for seven years. Write and run a C++ program that computes and displays a depreciation table for seven years. The table should have the form:
Social engineering is a form of hacking that has a social or political agenda behind it.
Answer the following statement true (T) or false (F)