List the types of local resource that are vulnerable to an attack by an untrusted program that is downloaded from a remote site and run in a local computer.
What will be an ideal response?
Objects in the file system e.g. files, directories can be read/written/created/deleted using the rights of the local
user who runs the program.
Network communication - the program might attempt to create sockets, connect to them, send messages etc.
Access to printers.
It may also impersonate the user in various ways, for example, sending/receiving email
You might also like to view...
Which of the following is a basic component of a sound wave?
A. frequency B. amplitude C. sample rate D. Both a and b
A catch block consists of four different elements: the keyword catch, followed by parentheses that contain an exception type and identifier, statements that take action to handle the error condition, an endcatch statement, and a return statement.
Answer the following statement true (T) or false (F)
The tags contain an important attribute called name that allows you to give each ____ a name.
A. frame B. window C. Web site D. file
?
?
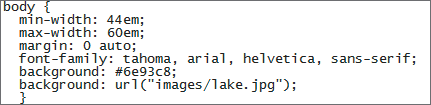
A. 44em B. 60em C. 0 D. You cannot tell from the figure.