Consider an application that must select dynamically an encryption algorithm based on security requirements and computing time constraints. Which design pattern would you select? Draw a UML class diagram depicting the classes in the pattern and justify your choice.
What will be an ideal response?
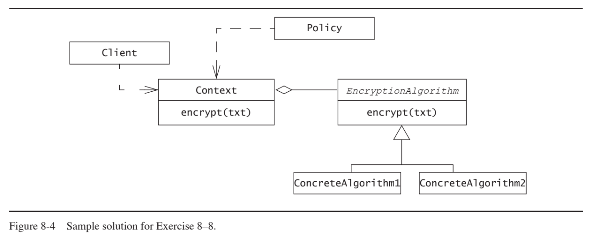
A strategy pattern can be used to address this problem. The EncryptionAlgorithm interface defines the common
interface that all encryption algorithms must comply with. A Policy class selects a concrete algorithm based on the
computing time constraints and the security requirements of the application. The Client interacts only with the
Context interface which stores the reference to the concrete algorithm.
You might also like to view...
It is an error to call the delete operator on a pointer a second time. Consider what happens if there is memory allocated on the free store for a class, a destructor, and initializing constructors have been defined, but no copy constructor was defined. Now suppose a function is called that has call-by-value parameters. Why does the program either die in the middle or give a segmentation fault?
What will be an ideal response?
Moving an item to a higher level in an outline is called demoting the item.?
Answer the following statement true (T) or false (F)
Case based critical thinking ? Case 13-4 ? Samantha is working on a web document. She wants to direct the browser to retrieve specific information about a URL, to reload the current page, and to load an entirely new page. ? Identify the object that Samantha should use to meet her desired requirements.
A. location B. option C. form D. string
The main suite of protocols used for transmitting data on the Internet is ________.
A. FTP B. TCP/IP C. SMTP D. POP