How does public key cryptography work?
What will be an ideal response?
Under PK cryptography, each party has a pair of keys. One key is private and must not be shared with anyone, and the other key is public and accessible by anyone. Under PK cryptography, when Alice wants to send a secure message to Bob, she encrypts the message using Bob's public key and sends the encrypted message to Bob. Bob then uses his private key to decrypt the message. On the other hand, when Bob wants to send a secure message to Alice, he encrypts the message using Alice's public key and sends the encrypted message to Alice. Alice also uses her private key to decrypt the message. Even with both public keys and encrypted messages, an eavesdropper cannot decrypt the messages because neither of the private keys is available. Typical key lengths for the RSA key pair-generation algorithm are 1,024 bits. It is not feasible to derive one member of the key pair from the other key.
You might also like to view...
Columnar forms and reports do not export to Word properly
Indicate whether the statement is true or false
You are having trouble remembering part of the correct format of a command. Which of the commands would give you help on the correct format of the parameters?
A) command * B) command ? C) command? D) help
Which type of IDPS works like antivirus software?
A. network-based B. anomaly-based C. host-based D. signature-based
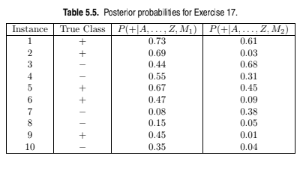
Repeat part (c) for model M1 using the threshold t = 0.1. Which threshold do you prefer, t = 0.5 or t = 0.1? Are the results consistent with what you expect from the ROC curve?
You are asked to evaluate the performance of two classification models, M1
and M2. The test set you have chosen contains 26 binary attributes, labeled
as A through Z.
Table 5.5 shows the posterior probabilities obtained by applying the models to
the test set. (Only the posterior probabilities for the positive class are shown).
As this is a two-class problem, P(?)=1 ? P(+) and P(?|A, . . . , Z)=1 ?
P(+|A, . . . , Z). Assume that we are mostly interested in detecting instances
from the positive class