What does the firewall do about packets that it suspects (but cannot prove) are attack packets?
A. It will quarantine the packet
B. It will pass the packet
C. It will challenge the sender of the packet
D. It will drop the packet
B. It will pass the packet
Computer Science & Information Technology
You might also like to view...
Prebuilt sets of instructions that perform tasks when a macro is run, called macro actions, are listed in the ________
A) Macro Library B) control grid C) Action Catalog D) Macro Catalog
Computer Science & Information Technology
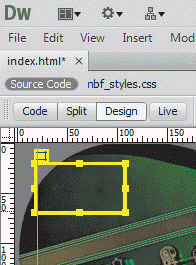 The yellow item in the accompanying figure can contain all of the following EXCEPT ____.
The yellow item in the accompanying figure can contain all of the following EXCEPT ____.
A. other divs B. multimedia content C. other Web pages D. forms
Computer Science & Information Technology
______ software helps businesses record and report financial transactions.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
What is a release methodology? Why is version control important?
What will be an ideal response?
Computer Science & Information Technology