How can you protect yourself against this kind of attack? What can cloud providers change to mitigate such attacks?
What will be an ideal response?
Some ways to protect oneself are to use fake or disposable information whenever possible; limit the providers you share information with; limit, to the extent possible, the overlapping information between accounts. Cloud providers can stop asking users for any information they don’t strictly need. They can also use other mechanisms to verify users that are more difficult for attackers to learn, guess, or steal, such as ones that prove your identity more directly (e.g., showing a valid driver’s license to a trusted party).
You might also like to view...
Write the code to declare a two dimension array of integers with 10 rows and 20 columns.
Fill in the blank(s) with the appropriate word(s).
The ability to capture and analyze all customer interactions, generate appropriate responses, and gather data to create and build effective and efficient marketing campaigns is known as contact management.
Answer the following statement true (T) or false (F)
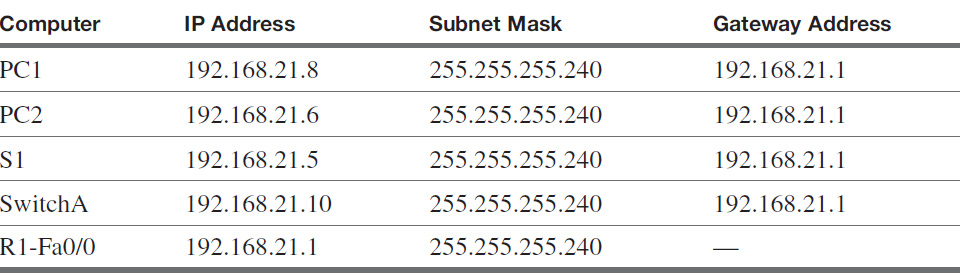
Configure the IP address settings for the router (R1), the computers (PC1 and PC2), and the switch (S1) for the network provided in Figure 1. Use the IP addresses provided in Table 1.
Which of the following is the location of the command to start the web server?
a. /etc/httpd/conf b. /var/httpd/conf c. /etc/init.d/httpd start d. /dev/init.d/httpd start