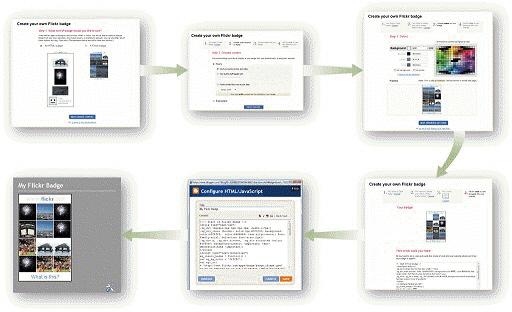
 In Step 1 in the accompanying figure, you confirm static HTML or animated Flash badge selection.
In Step 1 in the accompanying figure, you confirm static HTML or animated Flash badge selection.
Answer the following statement true (T) or false (F)
True
You might also like to view...
What does a hash function do?
a. A hash function computes an array index from the given key b. A hash function traverses the array c. A hash function computes the midpoint of the array d. A hash function deletes duplicates from the array
Justified text on screen can end up having large ribbons of black space running through it.
Answer the following statement true (T) or false (F)
The majority of business transactions, billions of them per day, are still done on ____________________ code that has now been updated and is likely to continue to run for the foreseeable future.
Fill in the blank(s) with the appropriate word(s).
Answer the following statement(s) true (T) or false (F)
6. In public cloud computing, the service provider can deliver increasing amounts of computing, network, and storage capacity on demand and without requiring any capital investment on the part of the cloud users. 7. Each private cloud has a defined set of available resources and users, with predefined quotas that limit how much capacity users of that cloud can consume. 8. The level of outsourcing risk is heightened as the organization increases the scope of processes being outsourced. 9. A good service-level agreement defines the customer’s right to audit the provider’s compliance and to conduct on-site inspections. 10. The service-level agreement (SLA) manager serves as the primary point of contact for any issues related to the delivery of the services covered in the SLA.