Good security programs begin and end with policy.
Answer the following statement true (T) or false (F)
True
Computer Science & Information Technology
You might also like to view...
Information is passed to a method in ________.
a. the method name b. that method’s return c. the method body d. the arguments to the method
Computer Science & Information Technology
The accompanying image is of a _____ dialog box in Microsoft Excel 2016.
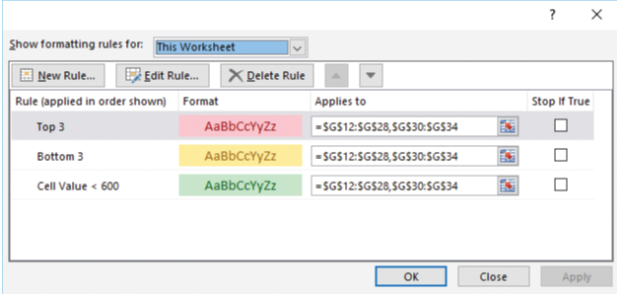
A. ?Workbook Formatting Rule B. ?Conditional Formatting Rules Manager C. ?File Formatting Rule D. ?Cell Formatting Rules Manager
Computer Science & Information Technology
A(n) ________ is a voice recording that plays and corresponds to the information on a slide
A) narration B) sound effect C) transition effect D) audio file
Computer Science & Information Technology
_____ is a radio-based wireless technology used to connect two or more devices together that are commonly within a close range of one another
Fill in the blank(s) with correct word
Computer Science & Information Technology