The ________ is used to setup a maintenance plan for running system tools
Fill in the blank(s) with correct word
Task Scheduler
You might also like to view...
Most physical security plans are developed separately from the planning that defines the activities of the information security process.
Answer the following statement true (T) or false (F)
FIGURE EX 1-1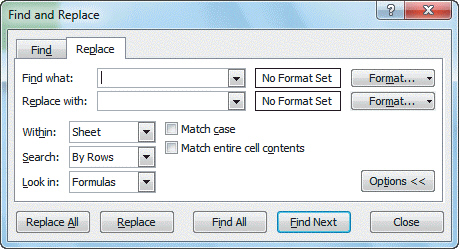 Referring to Figure EX 1-1 above, if you wanted to find an entry for an employee's name which may be misspelled, and you cannot remember if you capitalized the first and last name, you would choose the following search option: ____.
Referring to Figure EX 1-1 above, if you wanted to find an entry for an employee's name which may be misspelled, and you cannot remember if you capitalized the first and last name, you would choose the following search option: ____.
A. Match case B. Match entire cell contents C. both a. and b. D. neither a. nor b.
?What type of mobile forensics method listed by NIST guidelines involves looking at a device's content page by page and taking pictures?
A. ?Manual extraction B. ?Chip-off C. ?Micro read D. ?Logical extraction
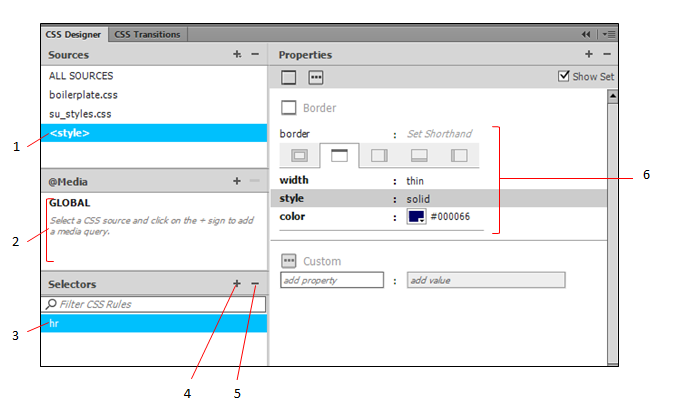
A. ?1 B. ?2 C. ?3 D. ?6