What is the purpose of the Masquerading section of the YaST Firewall module?
What will be an ideal response?
Masquerading is used to hide an internal network behind the firewall. With masquerading, the internal network can access the external network (such as the Internet) automatically. Any requests from the Internet to the internal network are blocked, however.
You might also like to view...
For the following sets of two-dimensional points, (1) provide a sketch of how they would be split into clusters by K-means for the given number of clusters and (2) indicate approximately where the resulting centroids would be. As- sume that we are using the squared error objective function. If you think that there is more than one possible solution, then please indicate whether each solution is a global or local minimum. Note that the label of each diagram in Figure 8.4 matches the corresponding part of this question, e.g., Figure 8.4(a) goes with part (a).
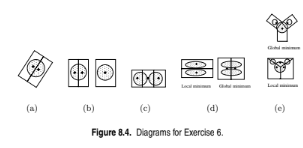
(a) K = 2. Assuming that the points are uniformly distributed in the circle,
how many possible ways are there (in theory) to partition the points
into two clusters? What can you say about the positions of the two
centroids? (Again, you don’t need to provide exact centroid locations,
just a qualitative description.)
(b) K = 3. The distance between the edges of the circles is slightly greater
than the radii of the circles.
(c) K = 3. The distance between the edges of the circles is much less than
the radii of the circles.
(d) K = 2.
(e) K = 3. Hint: Use the symmetry of the situation and remember that
we are looking for a rough sketch of what the result would be.
Suppose a and b are integer variables and we form the sum a + b. Now suppose c and d are floating-point variables and we form the sum c + d. The two + operators here are clearly being used for different purposes. This is an example of __________.
Fill in the blank(s) with the appropriate word(s).
A(n) ____ mouse uses an LED and computer chip to track a light beam as it bounces off a surface.
A. trackball B. laser C. optical D. elliptical
A horizontal line provides a way to add visual interest and differentiate sections of a Web page
Indicate whether the statement is true or false