A __________ is to try every possible key on a piece of ciphertext until an intelligible translation into plaintext is obtained.
A. mode of operation B. hash function
C. cryptanalysis D. brute-force attack
D. brute-force attack
You might also like to view...
A bibliography is the best way to plan and organize a larger document
Indicate whether the statement is true or false
Case 1Matthew has assigned a project to a new designer at XYZ Corporation. Matthew is working with the new designer to familiarize her with the contents of the dialog box shown below.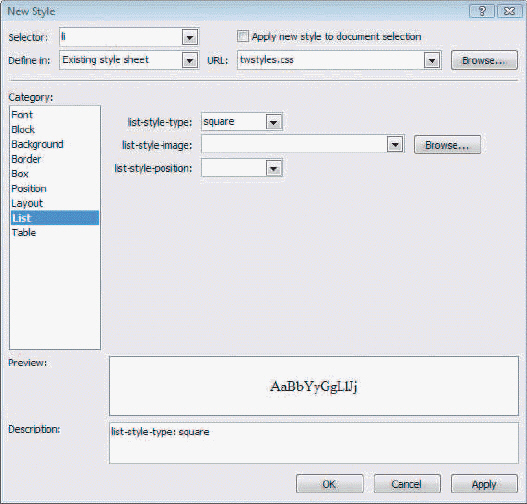 Referring to the figure above, which list should be selected to choose whether you want to define this style rule in an internal or external style sheet?
Referring to the figure above, which list should be selected to choose whether you want to define this style rule in an internal or external style sheet?
A. Define in B. Selector C. URL D. line-style-type
The three operational modes of a model law enforcement agency are incident response, ________ management, and prevention
Fill in the blank(s) with the appropriate word(s).
COGNITIVE ASSESSMENT Which of the following statements about data types is FALSE?
A. Yes/No fields can be used to create a field with True or False options. B. AutoNumber data types assign numbers automatically to each record. C. Text data types are used for lengthy memos. D. Object data types are used for photos, audio, or video.