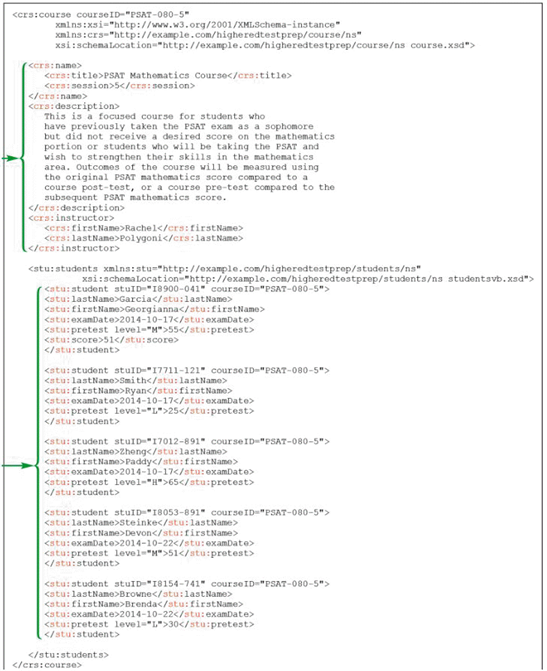
In the accompanying figure, the prefix _____ is added to opening and closing tags for all elements in the students namespace.
A. crs
B. stu
C. xml
D. xsi
Answer: B
You might also like to view...
What symbol do we use to represent a non-printable character?
What will be an ideal response?
Answer the following statements true (T) or false (F)
1. The use of 802.1X cannot prevent rogue access points and other unauthorized devices from becoming insecure backdoors. 2. The principal threats to wireless transmission are eavesdropping, altering or inserting messages, and disruption. 3. The use of encryption and authentication protocols is the standard method of countering attempts to alter or insert transmissions. 4. You should allow only specific computers to access your wireless network. 5. Security policies for mobile devices should assume that any mobile device will not be stolen or accessed by a malicious party.
Which of the following is NOT an option from the Delete arrow in the Comments group?
A) Delete all comments at one time B) Delete all comments shown C) Delete the current comment D) Delete only the recent comments
Which command would a technician use to diagnose DNS problems on a Windows computer?
A. nslookup B. ipconfig C. ping D. dig