Antivirus software scans virus signatures in e-mail attachments, ____, and files that you access from USB flash drives, CDs, DVDs, or the Web.
A. uploads
B. copies
C. backups
D. downloads
Answer: D
Computer Science & Information Technology
You might also like to view...
From Nancy's point of view, in order to restrict access, privacy is a zone of:
a) discretion. b) inaccessibility. c) nondisclosure. d) invisibility.
Computer Science & Information Technology
In the context of malware, what is remediation?
What will be an ideal response?
Computer Science & Information Technology
A newly installed floppy drive activity light stays on. Which of the following is the MOST likely problem?
A. The computer does not support this type of drive. B. Connector is plugged in backwards. C. Power is plugged in backwards. D. All floppies are corrupt.
Computer Science & Information Technology
Look at the Happy Cruise Lines database, for this question, consider only the following SHIP, PORT, and PASSENGER relations
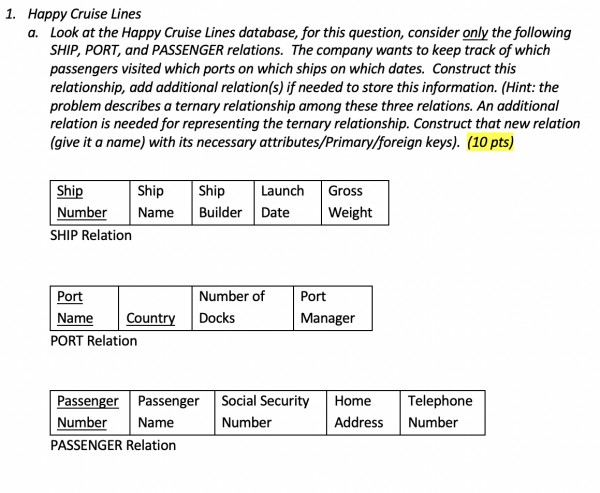
Computer Science & Information Technology