What type of software is silently installed on your computer, monitors your behavior, and performs actions based on your behavior?
A. Adware
B. Worm
C. Spyware
D. Virus
Answer: C
Computer Science & Information Technology
You might also like to view...
One of the most common ways of gaining unauthorized access to a network-based computer is by looking for ____ ports.
A. closed B. open C. unlocked D. scanned
Computer Science & Information Technology
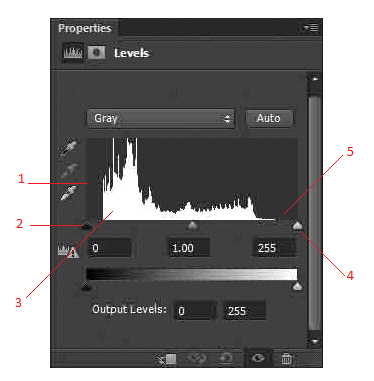 In the accompanying figure, item 4 points to the ____.
In the accompanying figure, item 4 points to the ____.
A. white point B. black point C. histogram D. grayscale point
Computer Science & Information Technology
Write a function to create a simple home page with your name, your picture, and a table with the titles of your courses and teacher names.
What will be an ideal response?
Computer Science & Information Technology
The performance of a binary search tree depends on the width of the tree.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology