Which of the following types of attacks is not normally considered a malicious code object?
a. Virus
b. DoS
c. Worm
d. Trojan horse
Answer: b. DoS
You might also like to view...
Fill in the blanks for the HTML code below to create a list as shown below.
1. Preheat oven to 450 degrees. 2. Heat butter and oil in a large saucepan. 3. Cook the shrimp for 10 minutes.
Which of the following is not a filter criterion for Network Monitor?
a. Frames captured by a specified network adapter b. Frames using a specified protocol c. Frames with a specified property, such as those originating from a specified IP address d. Frames containing only security information
What is the advantage of a distributed IDS?
A. A distributed IDS can collect data from one network device at a central manager console to allow a security manager to detect a more complex attack. B. A distributed IDS prevents all types of attacks. C. A distributed IDS can detect 100% of attacks. D. A distributed IDS can collect data from many devices at a central manager console to allow a security manager to detect a more complex attack.
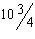 Which of the following would you not see when you click Item G in the accompanying figure to display the list of Preset Animations?
Which of the following would you not see when you click Item G in the accompanying figure to display the list of Preset Animations?
A. None B. All C. Fade In D. Rotate