Which of the following is the primary mechanism that the FTC uses to enforce privacy laws?
A. Civil litigation
B. Criminal litigation
C. Administrative enforcement action
D. Declaratory judgments
C. Administrative enforcement action
Computer Science & Information Technology
You might also like to view...
Videos can NOT be added to the background of a slide
Indicate whether the statement is true or false
Computer Science & Information Technology
____________________ is the process of checking user input data to make sure that it is complete and accurate.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
FIGURE 13-2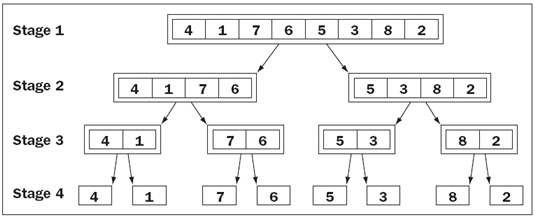 Figure 13-2 above shows subarrays generated during calls of ____.
Figure 13-2 above shows subarrays generated during calls of ____.
A. quickSort B. binarySort C. mergeSort D. bubbleSort
Computer Science & Information Technology
Normalization is usually viewed as a multistep process, moving the table structures from first normal form (1NF) to usually fifth normal form (5NF).
Answer the following statement true (T) or false (F)
Computer Science & Information Technology