What's the difference between recordable and rewritable versions of the CD, DVD and Blu-ray optical storage devices?
What will be an ideal response?
You can only record and store data once on the recordable versions of these devices. You can't erase or change any of the data you recorded although you can record more data before you finalize the device. Rewritable versions of these devices allow you to re-record different data multiple times.
You might also like to view...
(Computer Monitor Invoice GUI) In this exercise, you apply the GUI design guide- lines you have learned to a graphical user interface for an invoicing application (Fig. 3.24). You will specify the bounds of the JTextFields in the rows of the GUI that begin with the 15", 17" and 19" JLabels.
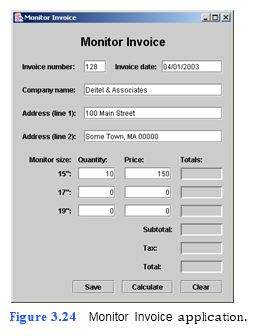
a) Copying the template to your working directory. Copy the C:Examples Tutorial03ExercisesMonitorInvoice directory to your C:SimplyJava direc- tory.
b) Opening the Command Prompt window and changing directories. Open the Com- mand Prompt by selecting Start > Programs > Accessories > Command Prompt. Change to your working directory by typing cd C:SimplyJavaMonitorInvoice, then pressing Enter.
c) Compiling the template application. Compile your application by typing javac
MonitorInvoice.java, then pressing Enter.
d) Running the template application. Run the application by typing java MonitorIn- voice. The GUI of the Monitor Invoice template application should appear as shown in Fig. 3.25.
e) Closing the application. Close your running application by clicking its close button. f) Opening the template file. Open the MonitorInvoice.java file in your text editor.
g) Customizing the JTextFields below the Quantity: JLabel. Using Fig. 3.24 and the template code
Which of the following is NOT a security recommendation when implementing SSH?
A. Change the port number in use from the default of 23. B. Only use version 2. C Disable root login to devices that have a root account. D. Control access to any SSH enabled device using ACLs, iptables, or TCP wrappers.
A sequential file update can only be processed serially starting at the beginning; it cannot be updated randomly.
Answer the following statement true (T) or false (F)
Which of the following options is NOT a major style category in Word?
A. Page B. Character C. Paragraph D. Linked