Acts of terrorism that involve premediated, politically motivated attacks against information, computer systems, computer programs, and data are referred to as ______.
a. cyberterrorism
b. religious terrorism
c. state-sponsored terrorism
d. international terrorism
a. cyberterrorism
You might also like to view...
We can generally assume that paraprofessionals have:
A) about the same skill level as volunteers. B) master's degrees or their equivalent. C) some limited training in areas where they work. D) little or no training in the area where they work.
There are four conduits we use to communicate messages. Which of the following is NOT one of these four conduits?
a. Orally b. Non-verbally c. Electronically d. Mutual understanding
Which of the following is a correctly stated null hypothesis?
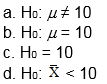
As soon as fingerprints were discovered to be a reliable means of identification, criminals began to devise ways to alter them so they could avoid being identified. American Public Enemy Number One in the 1930s, John Dillinger, burned his fingertips with a torch to change their appearance
a. True b. False Indicate whether the statement is true or false