Find the x- and y-intercepts of the equation and use them to sketch the graph. 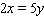
A. 
x-intercept ![]() , y-intercept none
, y-intercept none
B. 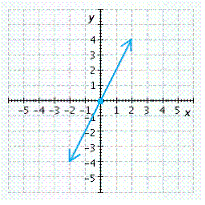
x-intercept ![]() , y-intercept
, y-intercept ![]()
C. 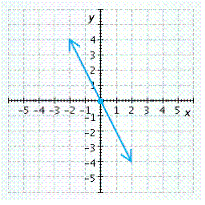
x-intercept ![]() , y-intercept
, y-intercept ![]()
D. 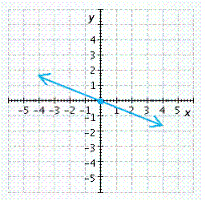
x-intercept ![]() , y-intercept
, y-intercept ![]()
E. 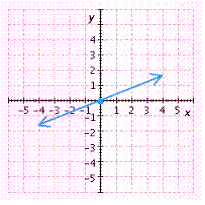
x-intercept ![]() , y-intercept
, y-intercept ![]()
Answer: E
Computer Science & Information Technology
You might also like to view...
The Report Wizard opens the new Report in ________ when the user finishes the wizard
Fill in the blank(s) with correct word
Computer Science & Information Technology
The ____ motion values precisely control an object's position and rotation throughout an animation.
A. X and Y B. Y and Z C. Up and Down D. Left and Right
Computer Science & Information Technology
What security functions typically are outsourced?
policy vulnerability testing Both policy and vulnerability testing Neither policy nor vulnerability testing
Computer Science & Information Technology
Arguably, ____________________ is one of the most essential blending modes.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology