Which of the following is not one of the three commands used to compile a program in Linux?
a. ./configure
b. make
c. compile
d. make install
ANS: C
You might also like to view...
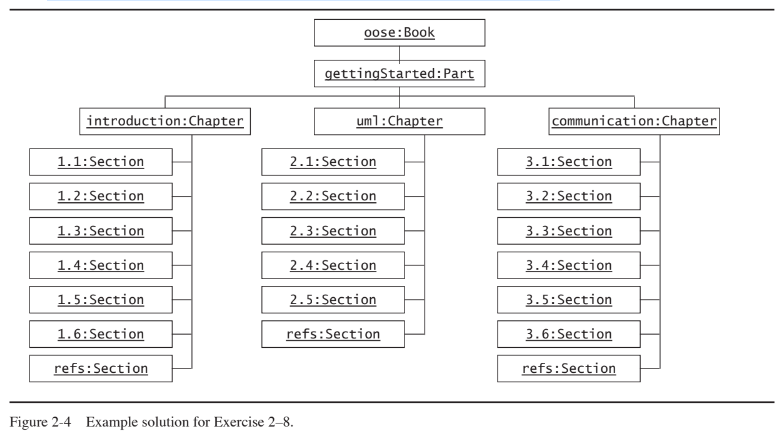
Draw an object diagram representing the first part of this book (i.e., Part I, Getting Started). Make sure that the object diagram you draw is consistent with the class diagram of Exercise 2–6.
To rename a category, click the ____ button in the Navigation Options dialog box.
A. Rename Category B. Rename Item C. Change Item D. Change Category
Which of the following IP addresses would a technician ping to verify the integrity of the local TCP/IP stack?
A. 10.0.0.1 B. 127.0.0.1 C. 169.254.0.1 D. 192.168.0.1
The most common variant of injecting malicious script content into pages returned to users by the targeted sites is the _________ vulnerability.
A. XSS reflection B. chroot jail C. atomic bomb D. PHP file inclusion