In the code that follows, the MIME type is
width="600" height="420">
data="videos/edinburgh.rm"
width="600" height="420">
a. videos/edinburgh.rm
b. edinburgh.rm
c. audio/x-pn-realaudio-plugin
d. x-pn-realaudio-plugin
c. audio/x-pn-realaudio-plugin
You might also like to view...
In order to maintain focus on the direction of the business, a practical lifecycle management model should be based on what?
A. Quality assurance B. Long-term goals C. Security D. Cost
How do Cascading Style Sheets allow an analyst to produce output?
What will be an ideal response?
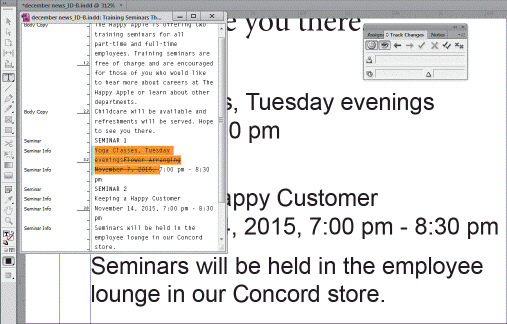 As shown in the accompanying figure, the Track Changes feature works by showing text edits highlighted in orange in the Story Editor window.
As shown in the accompanying figure, the Track Changes feature works by showing text edits highlighted in orange in the Story Editor window.
Answer the following statement true (T) or false (F)
A BYOD policy in which employees are able to access the wireless guest network is in effect in an organization. Some users however are using the Ethernet port in personal laptops to the wired network. Which of the following could an administrator use to ensure that unauthorized devices are not allowed to access the wired network?
A. VLAN access rules configured to reject packets originating from unauthorized devices B. Router access lists configured to block the IP addresses of unauthorized devices C. Firewall rules configured to block the MAC addresses of unauthorized devices D. Port security configured shut down the port when unauthorized devices connect