When not given any parameters, the su command is used to switch to the root user.
Answer the following statement true (T) or false (F)
True
Computer Science & Information Technology
You might also like to view...
A(n) ____________________ is a series of unique bytes that, like a fingerprint, uniquely identifies a malicious computer program and distinguishes it from legitimate files on your PC.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
How would you reverse two words?
What will be an ideal response?
Computer Science & Information Technology
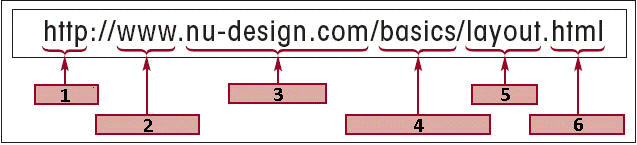 In the accompanying figure, the item marked ____ is the domain name.
In the accompanying figure, the item marked ____ is the domain name.
A. 1 B. 2 C. 3 D. 4
Computer Science & Information Technology
Primitive methods may be used to build more complex methods, or they may be run directly.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology