The concept of present possession suggests which of the following?
a. Just because those files were on a subject's computer, that doesn't mean the subject knew they were were.
b. Since the files are in the subject's possession, the assumption is that the subject knew they were there.
c. Because the file was knowingly moved from one location to another, the user knew the file was there.
d. The fact that the file exists on the hard drive proves that the user had direct access to the file.
c.
You might also like to view...
Malware that creates networks of infected computers that can be controlled from a central station is referred to as which of the following?
A. botnet B. Trojan C. logic bomb D. packet monkey
Morals are internal and a person should strive to behave well spontaneously is an example of the ________ ethical system
Fill in the blank(s) with correct word
Write an application that displays a solid square com- posed of a character input by the user (Fig. 12.29). The user also should input the size of the side of the square.
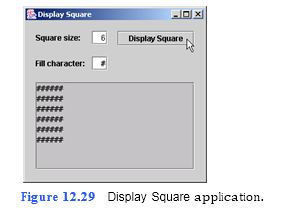
a) Copying the template to your working directory. Copy the C:Examples Tutorial12ExercisesDisplaySquare directory to your C:SimplyJava direc- tory.
b) Opening the template file. Open the DisplaySquare.java file in your text editor.
c) Adding a method to your application that displays a square of characters. On line
141, add a comment indicating that the method will display a square in a JTextArea. On line 142, add the method header for this method. The method will be called dis- playSquare. This method contains two parameters–the first, of type int, should be called size, the second, of type String, should be called character. This method does not return a value, but simply performs a task (displaying a square). For such methods, the return type is specified as void. Specify the return type for display- Square as void. On line 143, add a left brace to begin the body of the method. On line 145, add the right brace to end the body of the method. Follow the brace with a comment i
Which of the following is an example of a multilayer authentication?
A. A fingerprint scan and a smart card B. A retina scan and a password C. A retina scan and a fingerprint scan D. A password and a smart card