Both Linux and Mac OS X have been using one UAC function for a long time?it is called _______________.
Fill in the blank(s) with the appropriate word(s).
sudo
correct
You might also like to view...
Which of the following is the outcome of policy review?
A) Retirement or renewal B) Retirement or reauthorization C) Renewal or reauthorization D) None of the above
What type of exception would occur in the IA-32 architecture if a process attempts to divide by zero?
a) fault b) trap c) abort d) any of the above could occur
Office 365 requires passwords to consist of at least 8 to 16 characters, using a combination of upper- and lower-case letters, numbers, and symbols
Indicate whether the statement is true or false
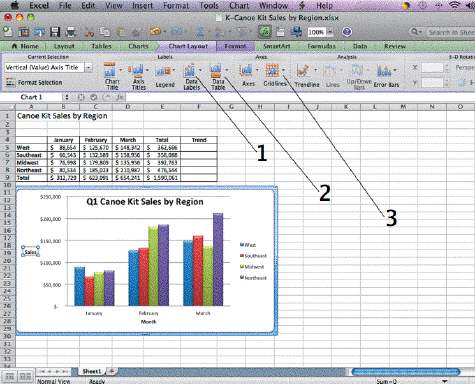 In the accompanying figure, Item 2 points to the button you click to add a Data Table, which is helpful when your ____ contains data from another worksheet or location.
In the accompanying figure, Item 2 points to the button you click to add a Data Table, which is helpful when your ____ contains data from another worksheet or location.
A. chart B. legend C. axes D. gridlines