Under which attack category does a UNIX Sendmail exploitation fall?
A. bad header information
B. single-packet attack
C. multiple-packet attack
D. suspicious data payload
Answer: D
You might also like to view...
Which of the following is NOT true about clustering?
A. failover is the ability to switch to a standby server if the active server fails B. load balancing allows servers to respond to an unexpected hardware or software failure C. clustering requires two or more identically-configured servers D. redundancy allows a system to continue running even if there is a failure
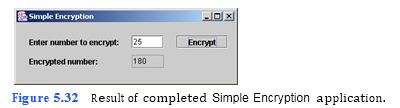
(Simple Encryption Application) This application uses a simple technique to encrypt a number. Encryption is the process of modifying data so that only those intended to receive the data can undo the changes and view the original data. The user inputs in a JTextField the number to be encrypted—this is often called the “plain text” value. The application then multiplies the number by 7 and adds 5 to encrypt the original number—this new value is Tutorial 5 Enhancing the Inventory Application 75 often called the “cypher text” value. The application displays the encrypted number in an uneditable JTextField as shown in Fig. 5.32. A user who receives the encr
a) Copying the template to your working directory. Copy the C:Examples Tutorial05ExercisesSimpleEncryption directory to your C:SimplyJava directory.
b) Opening the template file. Open the SimpleEncryption.java file in your text editor. c) Coding the encryptJButtonActionPerformed event handler. Scroll to the event
handler encryptJButtonActionPerformed (lines 98–101). Insert a statement that
gets the number in the enterJTextField, converts the number to an int and assigns the value to int variable plainText. Next, insert a statement that multiplies the number stored in variable plainText by 7 and adds 5, then stores the result in int variable cypherText. Finally, insert a statement that displays the value of cypher- Text in encryptedJTextField.
d) Clearing the result when a new value is input by the user. Locate the event handler enterJTextFieldKeyPressed (it appears immediately after the event handler encryptJButtonActionPerformed) in the template so
What specifically does the PowerPoint Save option allow you to do?
What will be an ideal response?
Describe a column chart and the suggested limits of this type of chart
What will be an ideal response?