Kerberos relies exclusively on __________ .
A. symmetric encryption
B. asymmetric encryption
C. private key encryption
D. public key encryption
A. symmetric encryption
You might also like to view...
Modify the script of Fig. 24.24 to use some of the string-related functions introduced in Section 24.7 to perform the validation instead of a regular expression. How does your new solution compare?
What will be an ideal response?
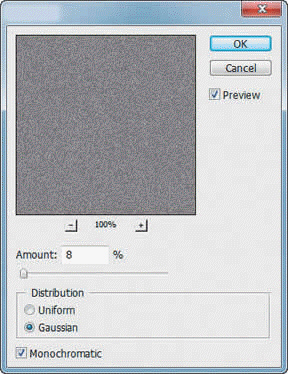 Which of the following can be accomplished by using the dialog box in the accompanying figure?
Which of the following can be accomplished by using the dialog box in the accompanying figure?
A. add sharpness to artwork B. create a consistent texture across an image C. both a. and b. D. neither a. nor b.
One application that uses multidimensional databases is an object-oriented database.
Answer the following statement true (T) or false (F)
FileChannel fc = null; Path file =Paths.get("C:\\Java\\Chapter.13\\RandomEmployees.txt"); ? Given the two declarations above, write a Java statement that creates a ByteChannel that is cast to a FileChannel. The file shoould be open for read and write operations.
What will be an ideal response?