____ enables authorization to be self-managed as an object owner can set permissions on all objects she or he created.
A. User-based authorization
B. Permissions inheritance
C. Administrative privileges
D. Discretionary access to securable objects
Answer: D
You might also like to view...
Find the error in the code segments, and explain how to correct it:
``` switch (n) { case 1: System.out.println("The number is 1"); case 2: System.out.println("The number is 2"); break; default: System.out.println("The number is not 1 or 2"); break; } ```
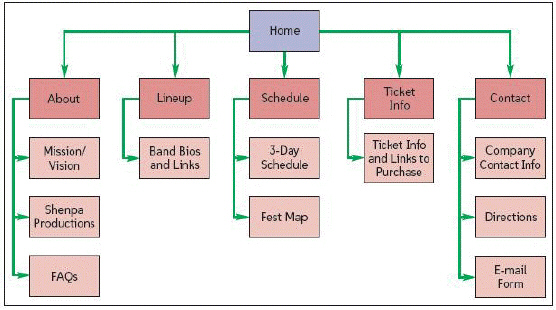 The accompanying figure shows a ____.
The accompanying figure shows a ____.
A. layout B. comp C. flowchart D. site metaphor
Critical Thinking QuestionsCase D-2The Flash project on which you are working is your final project for class, and it counts for 75 percent of your final grade. For this reason, you want to be able to fine-tune every detail of the animations with surgical precision. Which of the following resources allows you to control even the tiniest details of a motion tween? a. Tween Toolkitb. Motion Transformationc. Motion Editord. Tweening Resource
What will be an ideal response?
?Storing data on a hard disk is generally less convenient than storing data on a USB flash drive.
Answer the following statement true (T) or false (F)