List the two TCP/IP protocols used by earlier email systems to send and receive messages.
What will be an ideal response?
Earlier email systems use two TCP/IP protocols to send and receive messages: the Simple Mail Transfer Protocol (SMTP) handles outgoing mail, while the Post Office Protocol (POP, more commonly known as POP3 for the current version) is responsible for incoming mail.
You might also like to view...
The setMaximumRowCount method is used for:
a. Button. b. JComboBox. c. JRadioButton. d. JToggleButton.
Develop an application that calculates a salesperson’s commission from the number of items sold (Fig. 11.20). Assume that all items have a fixed price of 100 dollars per unit. Use a switch statement to implement the following sales commission schedule:
Fewer than 10 items sold = 1% commission
Between 10 and 39 items sold = 2% commission
Between 40 and 99 items sold = 3% commission
More than 99 items sold = 4% commission
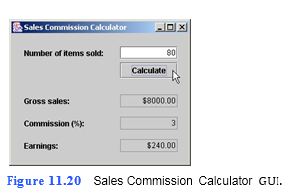
a) Copying the template to your working directory. Copy the directory C:Examples Tutorial11ExercisesSalesCommissionCalculator to your C:SimplyJava directory.
b) Opening the template file. Open the SalesCommissionCalculator.java file in your text editor. In the template, line 127 in the calculateJButtonActionPerformed method obtains the number of items sold that was entered by the user, converts the number to an int value and assigns the value to the int local variable items. Line 129 declares the double constant DOLLARS_PER_UNIT to represent the cost for each item sold. Line 132 creates the DecimalFormat variable dollars that will be used to for- mat the gross sales and the salesperson’s earnings for display purposes.
c) Calculate the gross sales. In calculateJButtonActionPerformed, insert a stat
In what manner were e-commerce employees caught making online purchases using clients' credit card numbers?
A) Saved files were stored in a hidden directory. B) Credit card numbers, along with the name and address of person who placed order, were found in a hidden HTML coded file. C) Copies of credit card numbers were found in their desks. D) Copies of transactions were found at their homes.
The Hyper-V ________ is a central location for managing your Hyper-V virtual hosts and the VMs running on those hosts
Fill in the blank(s) with correct word