A(n) ________ is a program that appears to be something useful or desirable but does something malicious in the background without your knowledge
Fill in the blank(s) with correct word
Trojan horse
You might also like to view...
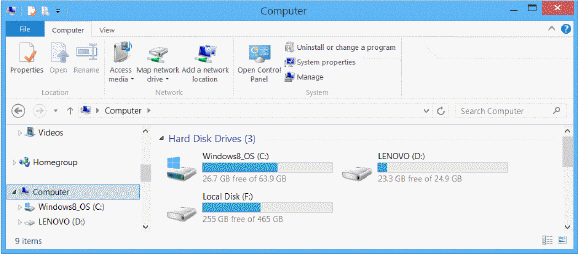 Referring to the accompanying figure, the hard drive is divided into two partitions, ________
Referring to the accompanying figure, the hard drive is divided into two partitions, ________
A. C and F B. C and D C. D and F D. There is only one partition, C.
What is a balanced binary search tree?
a. It's a binary search tree with the lowest possible number of levels b. It's one of the many implementations of a binary search tree c. It's a binary search tree without duplicated keys d. It's a binary search tree without duplicated values
If you deselect ____ in the Image Size dialog box, Photoshop will spread out the pixels over a larger area.
a. Nearest Neighbor b. Resample Image c. Bicubic d. Dithering
Children and young adults under 18 can easily become the victims of crimes due to their use of social media, but adults are entirely safe in using social media.?
Answer the following statement true (T) or false (F)