How can computer criminals use the Whois utility for their purposes?
What will be an ideal response?
The Whois utility is a commonly used tool for gathering IP address and domain information. With just a company's Web address, you can discover a tremendous amount of information. Unfortunately, attackers can also make use of this information. Often companies don't realize that they're publishing information on the Web that computer criminals can use. The Whois utility gives you information on a company's IP addresses and any other domains the company might be part of.
You might also like to view...
The relation shown in Figure 15.12 describes hospitals (hospitalName) that require certain items (itemDescription), which are supplied by suppliers (supplierNo) to the hospitals (hospitalName). Furthermore, whenever a hospital (h) requires a certain item (i) and a supplier (s) supplies that item (i) and the supplier (s) already supplies at least one item to that hospital (h), then the supplier (s) will also be supplying the required item (i) to the hospital (h). In this example, assume that a description of an item (itemDescription) uniquely identifies each type of item.
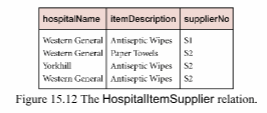
(a) Describe why the relation shown in Figure 15.12 is not in 5NF.
(b) Describe and illustrate the process of normalizing the relation shown in Figure 15.12 to 5NF.
____ allows limited use of copyright-protected work.
A. Derivation B. Trademark protection C. Fair use D. Intellectual property
________ sort order arranges numbers from the highest number to the lowest number
Fill in the blank(s) with correct word
The ____ determines how many colors are reproduced in a vector conversion.
a. curve threshold b. color threshold c. maximum color d. color valence