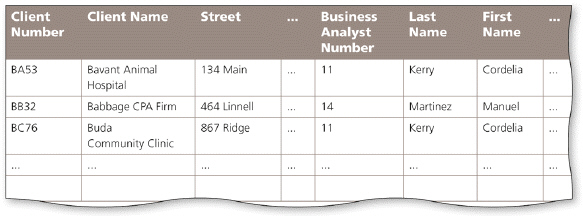
 In the accompanying figure, analyst names appear more than once in the table. Storing this data on multiple records is an example of redundancy which can cause several problems.What are these problems? What is the solution to the problem?
In the accompanying figure, analyst names appear more than once in the table. Storing this data on multiple records is an example of redundancy which can cause several problems.What are these problems? What is the solution to the problem?
What will be an ideal response?
Redundancy causes the following problems:
1. Wasted storage space. The same name is stored more than once. It should be stored only once.
2. More difficult database updates. If the same name is stored more than once and the individual's name changes, then the name would need to be changed in several different places.
3. A possibility of inconsistent data. There is nothing to prohibit a name being changed on one record and not on another.
The solution to the problem is to place the redundant data in a separate table.
You might also like to view...
Why is JavaFX preferred?
a. JavaFX is much simpler to learn and use for new Java programmers. b. JavaFX provides a multi-touch support for touch-enabled devices such as tablets and smart phones. c. JavaFX has a built-in 3D, animation support, video and audio playback, and runs as a standalone application or from a browser. d. JavaFX incorporates modern GUI technologies to enable you to develop rich Internet applications.
The ____ locates inappropriate information, such as comments, in a file and allows you to delete these slide elements.
A. Compatibility Checker B. Document Inspector C. Delete Elements Reviewer D. Comment Inspector
Match each term with the correct statement below.
A. data input into an encryption algorithm B. an attack that makes it appear that the wireless device and the network computers are communicating with each other C. an attack that attempts to prevent a device from performing its normal functions D. cryptographic keys that create a repeating pattern E. the process of changing ciphertext into plaintext F. a DoS attack that floods the RF spectrum with extraneous RF signal "noise" that prevents communications from occurring G. an imposter AP that is set up by an attacker H. data that has been encrypted I. the output from a pseudo-random number generator (PRNG) J. granting or denying approval to use specific resources
You can use database templates or you can create your own template for an Access database
Indicate whether the statement is true or false