The ________ tab includes information on the individual pieces of each program running on your system and the program to which they belong
A) App History
B) Networking
C) Processes
D) Performance
C
You might also like to view...
Case-Based Critical Thinking QuestionsCase 2 In his database of thousands of records, Suresh wants to standardize the format of certain fields. However, he does not want to store the formatting characters (e.g., parentheses, dashes, and slash characters). He decides to consult Sheila because she has extensive experience with input masks. Suresh wants to make letter entries optional in a license plate number field, as not all license plates have letters. What is the input mask character Sheila tells him to use?
A. L B. ? C. P D. !
In the accompanying figure of Microsoft Word 2016, Box A points to a(n) _____.?
?
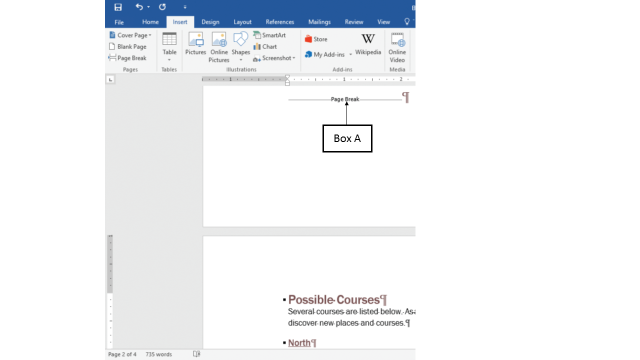
A. ?manual page break B. ?automatic page break C. ?odd page break D. ?even page break
____ are words determined by users to identify themselves in the digital world.?
A. ?Usernames B. ?Passwords C. ?Bytes D. ?PINs
You want a method of authentication for company-owned mobile devices in which users are required to use two-step authentication. Which of the following will best assist you in meeting this requirement?
A. Untrusted sources B. Authenticator apps C. Locator applications D. Failed login attempts