A common _______________ attack is where an attacker uses the telephone and convinces a user to give up secure information.
Fill in the blank(s) with the appropriate word(s).
social engineering
correct
Computer Science & Information Technology
You might also like to view...
Code that may be changed but is reinitialized each time it is used is said to be ________ .
a) serially reusable b) reentrant c) static d) shared
Computer Science & Information Technology
Acceptable-Use Internet Policies
What will be an ideal response?
Computer Science & Information Technology
In the following snippet of a Microsoft Excel 2016 worksheet, the information in cell B5 extends beyond the cell's border because:
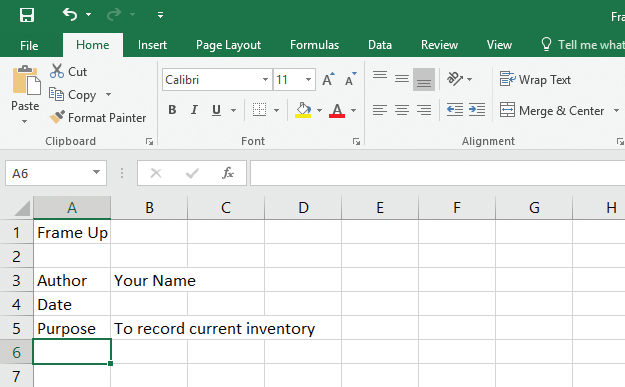
A. ?the cell borders have been removed. B. ?the text has been copied and pasted from a different cell. C. ?the cell next to it is empty. D. ?the format of row 5 allows text to spill over.
Computer Science & Information Technology
Expression Web uses XHTML-based templates called ____ Web templates.
A. superior B. dynamic C. fast D. quality
Computer Science & Information Technology