A _____ is the principal means of controlling access to computer and network resources and rights or privileges.
A. Group policies
B. Network policies
C. User account
D. UAC
Answer: C. User account
You might also like to view...
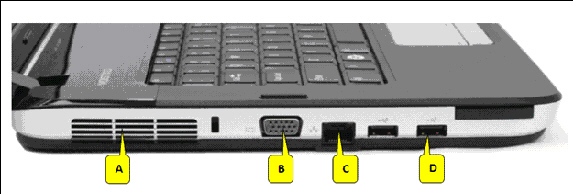 Referring to the accompanying figure, which of the following callouts points to the port where you can plug in a USB hub?
Referring to the accompanying figure, which of the following callouts points to the port where you can plug in a USB hub?
A. A B. B C. C D. D
A ________ Identifier is a unique number assigned to each process when it runs
Fill in the blank(s) with correct word
Case-Based Critical Thinking QuestionsCase 3-2Maureen's brother Paul has also been researching cruise ships online and has created his own presentation. Maureen and Paul decide to work together to create a great presentation to show the rest of the family. Paul sends Maureen his slides about offshore excursions and, following the simplest strategy available to her, she ____.
A. embeds them into her presentation B. uses the Reuse Slides task pane to incorporate his slides into her presentation C. copies and pastes his slides into her presentation D. appends them to her presentation
To enter data in a cell, you must first select or activate the _____.
A. row B. worksheet C. column D. cell