Define polymorphism, and provide three examples.
What will be an ideal response?
Polymorphism is the concept that a message can have different meanings to different objects. For example the message GOOD NIGHT signals the PARENT object to read a bedtime story, but the same message to the DOG object tells the dog to go to sleep. The GOOD NIGHT message to the CHILD object signals it to get ready for bed.
You might also like to view...
In order to ensure that the strategic management plan is composed of tangible activities, it is documented using a ____ process.
A. bottom-up B. top-down C. middle-out D. sides-in
What is a primary color? A secondary color? A tertiary color?
What will be an ideal response?
Write an application that encrypts a message from the user (Fig. 23.18). The application should be able to encrypt the message in two different ways: substitution cipher and transposition cipher (both described below). The user should be able to enter the message in a JTextField and select the desired method of encryption. The encrypted message is then displayed in an uneditable JTextField. In a substitution cipher, every character in the English alphabet is represented by a dif- ferent character in a substitution String, which we will refer to as the substitution alphabet. Every time a letter occurs in the English sentence, it is replaced by the letter in the corre- sponding index of the substitution String. As an example of a substitution cipher, let’s e
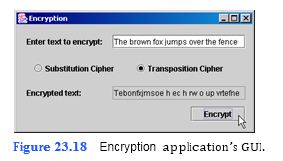
a) Copying the template to your working directory. Copy the C:Examples Tutorial23ExercisesCipherEncryption directory to your C:SimplyJava directory.
b) Opening the template file. Open the Encryption.java file in your text editor.
c) Adding code to the substitutionCipher method. In the substitutionCipher method (lines 126–140), English and substitution alphabet Strings have been declared for you as normalAlphabet and cipherAlphabet, respectively. Other Strings that you will be using have already been defined for you—cipher is an empty String you will use to store the encrypted text and plain contains the text entered by the user. After the declaration of the Strings, add an empty for state- ment that loops for each character in plain.
d) Performing the substitution encryption. Inside the for statement you added in Step c, create an int variable index and assign to it the index in normalAlphabet where the current character in plain
Which Cisco IOS command is used to configure a specific interface to be included in the OSPFv3 routing process?
A) network ipv6-prefix/ipv6-prefix-length area area-id B) ipv6 ospfv3 process-id area area-id C) ipv6 ospf process-id area area-id D) network ipv6-prefix/ipv6-prefix-length