________ code is not modified as it executes and may be shared by several processes simultaneously.
a) Preemptible
b) Dynamic
c) Reentrant
d) Serially reusable
c) Reentrant
Computer Science & Information Technology
You might also like to view...
For the following Web page, list all of the objects and actions
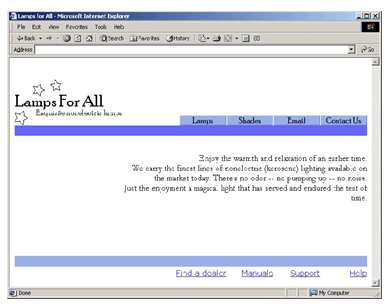
Computer Science & Information Technology
Which one of the following statements is true?
a. a terabyte is larger than a petabyte. b. a kilobyte is exactly 1000 bytes. c. a gigabyte is 1024 megabytes. d. an exabyte is 1024 zettabytes.
Computer Science & Information Technology
Which of the following commands can be used to obtain a hash of the original drive and the forensic copy?
A) dd B) netcat C) md5sum D) nc
Computer Science & Information Technology
A CIDR block contains the subnets with the following IP addresses:
192.168.68.0/22 192.168.69.0/22 192.168.70.0/22 192.168.71.0/22 Are there any problems with this group of subnets in the CIDR block? Show your work.
Computer Science & Information Technology