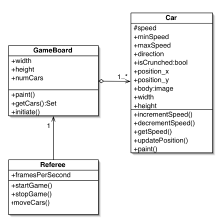
Analysis: Initial Object Model for GameBoard, Referee and Car
What will be an ideal response?
You might also like to view...
Special methods ________,_________ and __________ control attribute access through the [] subscript operators for list- and dictionary-like types.
Fill in the blank(s) with the appropriate word(s).
Identify four things that you can do to deter or minimize the impact of theft or intentional damage to your computer?
What will be an ideal response?
John has subscribed to a cloud-based service to synchronize data between his smartphone, tablet, and PC. Before allowing the data to be synchronized, this service uses a process in which the cloud service and the client on the smartphone will verify the security of all devices’ security certificates. What type of security does the cloud-base service employ?
A. Mutual authentication B. VPN C. IMAP D. Tethering
The typedef statement creates a new data type.
Answer the following statement true (T) or false (F)