Write the syntax of a tcpdump command that captures packets containing IP datagrams with a source or destination IP address equal to 10.0.1.12.
What will be an ideal response?
![]()
You might also like to view...
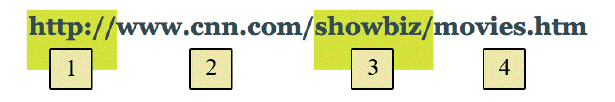 In the figure above, the Web folder name is represented by ____.
In the figure above, the Web folder name is represented by ____.
A. item 1 B. item 2 C. item 3 D. item 4
The client can use a method without knowing how it is implemented. The details of the implementation are encapsulated in the method and hidden from the client who invokes the method. This is known as
a. information hiding b. encapsulation c. method hiding d. simplifying method
____ content accepts and responds to human actions using multimedia elements.
A. Navigational B. Active C. Authored D. Interactive
Which of the following is true regarding bag operations as a physical method of identity theft?
a. They include sifting through commercial or residential trash or waste for information deemed valuable. b. They are typically conducted by the host government's security or intelligence services. c. They are executed by depositing personal documents in unlocked containers on the side of the road until they are retrieved. d. They involve the creation of shell companies that engage in the collection of personal financial information.