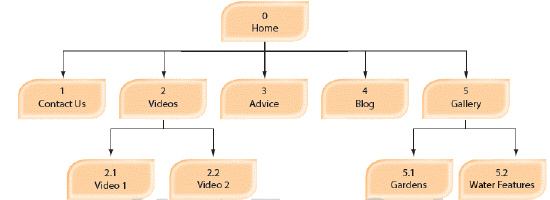
 What is the accompanying figure an example of?
What is the accompanying figure an example of?
A. timeline
B. wireframe
C. deliverables
D. resources
Answer: B
Computer Science & Information Technology
You might also like to view...
A hacker is an individual who gains unauthorized access to computer systems for the purpose of corrupting or stealing data
Indicate whether the statement is true or false
Computer Science & Information Technology
A shape that has been added to the ________ displays on every slide in a presentation
Fill in the blank(s) with correct word
Computer Science & Information Technology
The most obvious limitation of midsquare hashing is ____.
A. its inefficiency B. the size of the key C. the high number of collisions D. the high processing requirements
Computer Science & Information Technology
Scanning techniques are split into ________ categories.
A. three B. five C. four D. two
Computer Science & Information Technology