The _________ attack is designed to circumvent filtering rules that depend on TCP header information.
A. ?source routing ?
B. ?IP address spoofing
C. ?network layer address spoofing ?
D. ?tiny fragment
D. ?tiny fragment
You might also like to view...
How do pixel-based and vector-based animation formats differ in how they represent images?
What will be an ideal response?
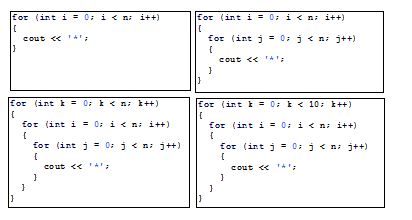
How many stars are displayed in the following code if n is 10? How many if n is 20? Use the Big O notation to estimate the time complexity.
The process that computes the bounds of the shapes of colors within a bitmap image and then derives the polygon object that describes that image is called ____________________.
Fill in the blank(s) with the appropriate word(s).
An administrator is replacing a wireless router. The configuration of the old wireless router was not documented before it stopped functioning. The equipment connecting to the wireless network uses older legacy equipment that was manufactured prior to the release of the 802.11i standard. Which of the following configuration options should the administrator select for the new wireless router?
A. WPA+CCMP B. WPA2+CCMP C. WPA+TKIP D. WPA2+TKIP