Explain three safeguards you can use to secure your wireless networks like the kind in the accompanying figure.
What will be an ideal response?
Student responses will vary, but should be drawn from the following information from the text.
• Immediately upon connecting your wireless access point and/or router, change the password required to access administrative features. If the password remains at its default setting, others may possibly be able to connect to and configure your wireless network settings.
• Change the SSID (service set identifier), which is a network name, from the default to something that uniquely identifies your network, especially if you live in close proximity to other wireless networks.
• Do not broadcast the SSID. This will make it more difficult for others to detect your wireless network. When you want to connect a computer or mobile device to your wireless network, it will be necessary to enter the SSID manually.
• Enable an encryption method such as WPA2 (Wi-Fi Protected Access 2), and specify a password or passphrase that is difficult for others to guess. Passwords and passphrases that are more than eight characters, contain uppercase and lowercase letters, numbers, and special characters are the most secure.
• Enable and configure the MAC (Media Access Control) address control feature. A MAC address is a unique hardware identifier for your computer or device. The MAC address control feature specifies the computers and mobile devices that can connect to your network. If a computer or device is not specified, it will not be able to connect.
• Choose a secure location for your wireless router so that unauthorized people cannot access it. Someone who has physical access to a wireless router can restore factory defaults and erase your settings.
You might also like to view...
Describe when the joint review activity is conducted and the purpose of the review.
What will be an ideal response?
What happened to the files in the Recycle Bin?
What will be an ideal response?
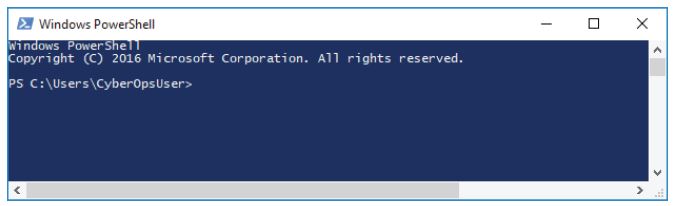
Step 1. Access PowerShell console.
a. Click Start. Search and select powershell.
b. Click Start. Search and select command prompt.
Step 2. Explore Command Prompt and PowerShell commands.
a. Enter dir at the prompt in both windows.
b. Try another command that you have used in the command prompt, such as ping, cd, and ipconfig.
Step 3. Explore cmdlets.
a. PowerShell commands, cmdlets, are constructed in the form of verb-noun string. To identify the PowerShell command to list the subdirectories and files in a directory, enter Get-Alias dir at the PowerShell prompt.
```
PS C:UsersCyberOpsUser> Get-Alias dir
CommandType Name Version
Source
----------- ---- -------
------
Alias dir -> Get-ChildItem
```
b. For more detailed information about cmdlets, navigate to https://technet.microsoft.
com/en-us/library/ee332526.aspx.
c. Close the
Tabs are small boxes of text that can be added to a cell
Indicate whether the statement is true or false
To prevent running an action query accidentally, use the Run button to view the selected records.
Answer the following statement true (T) or false (F)