How is scoping used to ensure a proper balance between the degree of protection and the assumed level of a threat?
Fill in the blank(s) with the appropriate word(s).
Through the use of controls based on a system's assessed status in FIPS 199
You might also like to view...
Dragging the vertical scroll bar does which of the following?
A) Shows a subset of Ribbon commands B) Displays Word Options C) Repositions the insertion point D) Displays another part of the document but does not move the insertion point
The purpose of a _____ is to provide a way for a third-party Web site to place cookies from that third-party site on a visitor's computer. Select one:
A) personal firewall B) digital certificate C) Web bug D) gateway server
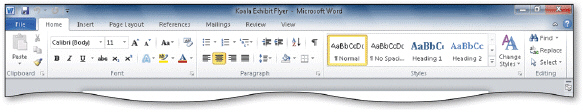 As shown in the accompanying figure, each ____ contains a collection of groups, each of which contains related functions.
As shown in the accompanying figure, each ____ contains a collection of groups, each of which contains related functions.
A. cluster B. matrix C. tab D. base
To use a cookie or other text string encoded with theencodeURIComponent()function, you must first decode it with the __________ function.
Fill in the blank(s) with the appropriate word(s).