How do operating systems solve the problem of a thief stealing a password file and seeing that his password and another password hash to the same value?
What will be an ideal response?
Because this would give the thief a better than random chance of guessing the other person's password, some operating systems keep a third entry for each user in the password file, namely the exact time at which the user created the password. This timestamp gets appended to the original password, and the result is then run through the encryption algorithm. That way, two identical passwords do not hash to the same value because the probability that they were created at the exact same instant in time is infinitesimally small.
You might also like to view...
Given the following function definition
void shift(int& a, int&b) { a=b; b=a; } What is the output after the following function call? int first=0, second=10; shift(first, second); cout << first <<" "<< second << endl; a. 0 10 b. 10 0 c. 0 0 d. 10 10
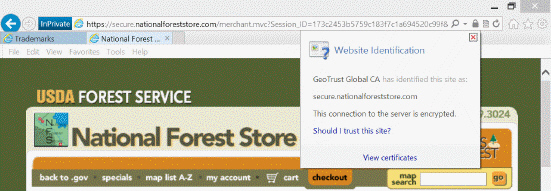 Referring to the accompanying figure, which of the following icons should you click to view a digital certificate?
Referring to the accompanying figure, which of the following icons should you click to view a digital certificate?
A. ![]()
B. ![]()
C. ![]()
D. ![]()
The VBA debugger allows the programmer to perform all of the following tasks EXCEPT:
A) Continue execution of the code. B) Halt execution of the code. C) Delete each line of code. D) Enter VBA code in the Immediate window to view the results.
How can the following algorithm be described? position = 0while position < len(lyst): if target == lyst[position]: return position position += 1return -1
A. binary search B. bubble sort C. sequential search D. selection sort