Using a process known as ____, network-based IDPSs look for attack patterns by comparing measured activity to known signatures in their knowledge base to determine whether or not an attack has occurred or may be under way.
A. packet sniffing
B. port monitoring
C. traffic measurement
D. signature matching
Answer: D
You might also like to view...
Too fast a cutting speed results in ____.
A. the top edge of the plate being melted or rounded off B. an incomplete cut C. the sides of the kerf being slightly dished D. gouges in the side of the cut
Label J represents
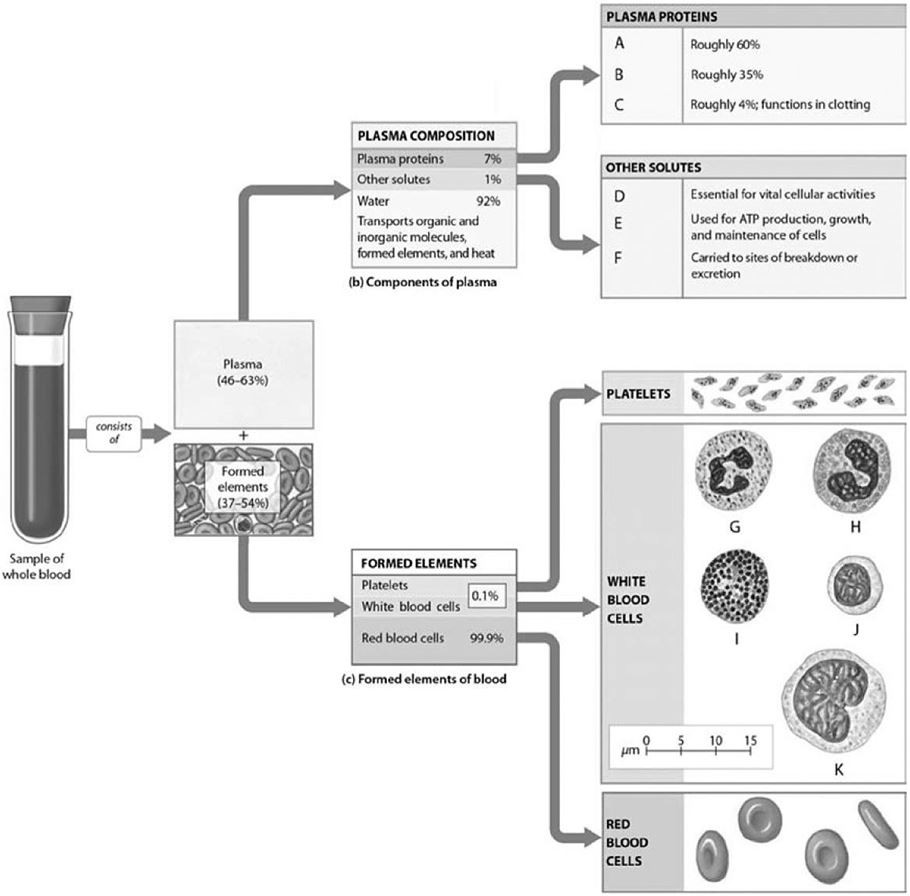
A) basophils.
B) neutrophils.
C) monocytes.
D) eosinophils.
E) lymphocytes.
Market hog prices increase and decrease based on the ratio of:
A. boar to sow B. lean to fat C. underline to underside D. conformation to finish
The most common airflow problem experienced on air conditioning systems is
A) Low airflow caused by dirty or plugged air filters B) Excessive airflow caused by removing the air filter and not replacing it C) Excessive airflow caused by high operating voltage D) Low airflow caused by unusually low barometric pressure