What are security audits meant to do?
What will be an ideal response?
Security audits are meant to provide an accurate view of the organization's internal security controls and to initiate positive changes for identified weak areas.
You might also like to view...
An __________ is any device that includes a computer chip, but that is not a general-purpose computer, such as a laptop or desktop system
Fill in the blank(s) with the appropriate word(s).
In a mail merge, the document that contains the text that remains constant is the ________ document
Fill in the blank(s) with correct word
What are the pros and cons of using a layered network architecture?
What will be an ideal response?
FIGURE EX 3-1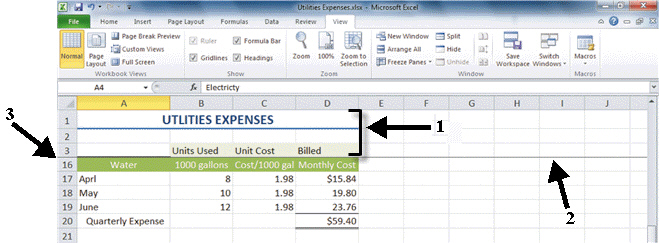 The area marked with the number 3 in Figure EX 3-1 above, shows ____scrolled out of view.
The area marked with the number 3 in Figure EX 3-1 above, shows ____scrolled out of view.
A. rows 3 through 16 B. rows 4 through 15 C. columns A through D D. columns B through D