COGNITIVE ASSESSMENT
The term back door, as it refers to computer crime, is _____________.
A. the area of memory where information about a virus or attempted attack is sent by the antivirus software in order to prevent similar attacks in the future
B. a program or set of instructions that allows users to bypass security controls when accessing a program, computer, or network
C. the vulnerabilities of a computer criminal or criminal network that enable them to be tracked and caught
D. a weakness in a computer or network's security system that enables criminals to gain unauthorized access
Answer: B
You might also like to view...
Any process that the parent process forks is a________process.
a) sub-. b) child. c) descendent. d) None of the above.
How could email be sent to a list of 100 recipients using PGP or a similar scheme? Suggest a scheme that is simpler and faster when the list is used frequently.
What will be an ideal response?
Create an application that stores people’s names and birthdays in a file (Fig. 25.49). The user creates a file and inputs each person’s first name, last name and birthday in the application. The information is then written to the file, as shown in the right image of Fig. 25.49. Note that only the month and day are written to the file.
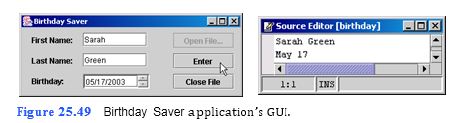
a) Copying the template to your working directory. Copy the directory C:Examples Tutorial25ExercisesBirthdaySaver to your C:SimplyJava directory.
b) Opening the template file. Open the BirthdaySaver.java file in your text editor.
c) Viewing the PrintWriter instance variable. In lines 29–30, view the PrintWriter
instance variable named output that will be used to write output to a file.
d) Opening a JFileChooser dialog. For this exercise, you will define only the open- FileJButtonActionPerformed method (lines 160–163 in the template). Functional- ity for writing data to a file and closing a file is provided in the template. Starting on line 163, add and display a new JFileChooser to allow the user to select the file to which to write. Then, define an if statement that causes the method to be exited if the user clicks the Cancel JButton.
e) Validating the file name. Retrieve the file selected by the user (as a File object) and the name of the file. Create a File object, selectedFile
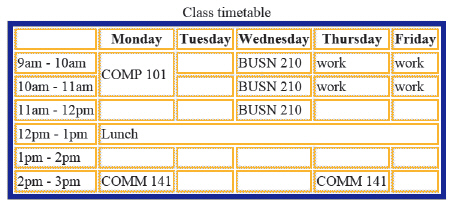 In the accompanying figure, the cell with the "Lunch" contents is an example of the use of a ____ attribute.
In the accompanying figure, the cell with the "Lunch" contents is an example of the use of a ____ attribute.
A. rowspan B. colspan C. merge D. spanrow