What is the OCTAVE Method approach to risk management?
What will be an ideal response?
The Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE) Method is an InfoSec risk evaluation methodology that allows organizations to balance the protection of critical information assets against the costs of providing protective and detection controls. This process can enable an organization to measure itself against known or accepted good security practices and then establish an organization-wide protection strategy and InfoSec risk mitigation plan.
You might also like to view...
The method distance vector protocols use to prevent packets from endlessly circulating around a routing loop is called ____________________.
Fill in the blank(s) with the appropriate word(s).
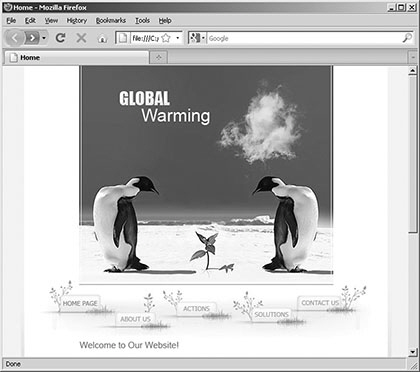 In the figure above, the Web browser would be expecting you to type a ____ into the area that says file:///?
In the figure above, the Web browser would be expecting you to type a ____ into the area that says file:///?
A. parser engine B. file type C. Web address D. Web agent
AutoPlay refers to the default action that occurs when you?
A. ?play music. B. ?connect a device. C. ?unlock the sign-in screen. D. ?open a browser window.
Which normal form will remove dependencies on a non-key field?
What will be an ideal response?