Which of the following is not one of the DoS attack types?
a. Gaining access
b. Bandwidth consumption
c. SYN Flood attacks
d. Program and application attacks
ANS: A
You might also like to view...
(Drawing Patterns with Nested for Loops) Write a program that uses for statements to print the following patterns separately, one below the other. Use for loops to generate the patterns. All asterisks (*) should be printed by a single statement of the form cout << '*'; (this causes the asterisks to print side by side). [Hint: The last two patterns require that each line begin with an ap- propriate number of blanks. Extra credit: Combine your code from the four separate problems into a single program that prints all four patterns side by side by making clever use of nested for loops.]
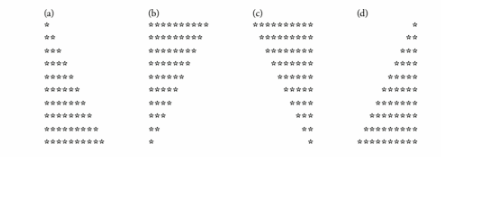
What will be an ideal response?
The first step in creating the initial form is to:
A) use the Ctrl key to select multiple fields and then add them all at once to a blank form. B) drag the fields to the blank form one at a time. C) click the Blank Form icon in the Create tab of the Ribbon. D) click the plus sign next to the table to show all the fields in this table.
________ happens when a right held by a copyright owner is used without permission of the owner
A) Infringement of copyright B) Theft of services C) Piracy D) Plagiarism
All of the following statements are TRUE about importing XML data EXCEPT:
A) XML is an increasingly popular tool working behind the scenes in Excel. B) XML allows users to define their own tags in order to define the content of the document. C) XML and HTML are examples of markup languages. D) Most web pages are programmed in XML.